2nd November 2010
Blog >> 10 Steps to Secure Your Web Hosting Account
It's a common assumption to think that your host is taking care of your website's security, the truth is they are, but that doesn't mean there aren't plenty of steps you can take to enhance and improve the security of your web hosting account.
Step 1. Your Username and Password

|
Password Statistics
|
- The most commonly used password is password1.
- 52% of people never change their passwords unless required to do so.
- 66% of US consumers use only 1-2 different passwords.
- 42% of Hotmail users use passwords containing only lowercase letters.
- 19% of Hotmail users use passwords containing only numbers.
- Nearly 1% of Hotmail users use the password 123456.
|
|
|
It may seem obvious that the security of your login credentials for FTP, your control panel and so fourth is important, but approximately 42% of users use simple text passwords without numbers or symbols.
It's also frighteningly common that users use their username as their password. When you consider the username usually forms part of the server directory path and the fact that this is disclosed in environmental variables, then you realise they may as well not use login details.
For a basic level of security your username and password should always meet the following criteria:
- Minimum 8 characters in length, preferably 10 or more.
- Contains both capital and lowercase characters.
- Contains at least 1 numeric character.
- Does not contain any dictionary words.
- Is not used for any accounts with third-party websites/services.
For increased security your username and password should meet the following criteria:
- Contains at least 3 numbers which are not grouped.
- Contains at least 2 non-alphanumeric characters/symbols which are not grouped.
- Does not contain more than 3 characters which may form part of a word.
You should endeavour to change your passwords regularly to ensure their security is maintained.
For assistance generating a secure random password we have provided a convenient random password generator:
Step 2. Lock Your FTP Account
Many hosting companies now enable you to secure your FTP account, either enabling access for short periods of time via a control panel or restricting access by IP address. If possible, you should always disable FTP access when you're not using it to ensure it can not be attacked.
Step 3. Use Secure FTP
Rather than using standard FTP you should use SFTP to ensure all data transfer is secure. Most hosting companies support secure FTP usually via port 22 - simply update your FTP software settings to use SFTP and the appropriate port and all your data transfer will be secured.
If your FTP software does not support SFTP, try Filezilla or WinSCP:
Step 4. Lock Down Your File Permissions
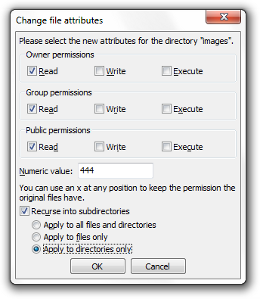
If you use a Linux/Unix web server then you can set permissions on each file and directory which control which users and groups within the system can access the files. You should familiarise yourself with your file permissions to ensure your file structure is secure, for example setting the permissions to 777 will allow access for any user on the system, unless another permissions system is limiting access.
You should avoid settings open permissions such as 777, 775, 755, 666, 664 or 644. It's good practice to set your directories to 555 (all read and execute) and files to 444 (all read) unless you need to open access to a specific user/program. Depending on your server configuration this may not be a possible so please check with your system administrator for advice specific to your hosting environment.
Step 5. Clean Your Files
You should check your files and directory structure regularly to ensure they are not disrupted. Always check any unusual files which you do not recognise as it is possible these have been created by a malicious user, you may also like to consider restoring your PHP files on a routine basis incase any malicious code has been added.
You can use a file integrity checker such as AIDE (Advanced Intrusion Detection Environment) to scan and audit your file structure, and notify you to any changes or anomalies:
Step 6. Check Your Logs
You should check your system logs for suspicious activity on a regularly basis, including your error logs and visitor access logs. Various tools exist to help you audit your logs, but a basic check using your web site statistics software (e.g. Webalizer or AWStats) will often highlight key issues such as hot linking:
Step 7. Keep Software Up-To-Date & Install Server Updates

|
Website Vulnerability Statistics
|
- 70% of websites are open to cross-site scripting attacks.
- 50% of all websites are subject to information leakage attacks.
- 25% of websites are subject to phishing and content spoofing attacks.
- 20% of websites are unprotected against SQL injection.
|
|
|
If you're using third-party software such as WordPress or Joomla then you must ensure you keep up-to-date with the latest releases. Software updates usually include security fixes which are documented in the release notes, this means a malicious user can simply use the release notes as instructions for hacking your website! Keeping your software up-to-date is critical for ensuring you don't leave security holes open.
If you are responsible for your server configuration and management then you must ensure you install the latest operating system and software updates. As with software, any operating system security fixes are usually well documented and therefore extremely easy to exploit.
If you are not responsibly for your server configuration and management then you should build a strong relationship with your hosting provider and ensure they are regularly updating your server's operating system and software.
Step 8. Use a Reputable Hosting Service
Many web hosting companies are simply interested in the quantity of customers they can get, and not in the quality of service and support that they offer. It's worth paying a little extra and using a reputable web hosting service which provides comprehensive service and support, and which you can build a strong working relationship with.
For those of you who require dedicated servers or VPS hosting solutions, we highly recommend ServINT whom we have used for many years. We also recommend Bluehost and Heart Internet:
Step 9. Use a Server Auditing Service
If you are concerned about the security of your website/server then you should consider using a server auditing service. There are numerous online services and software applications which fully automate the process of auditing your server, scanning for everything from XSS attacks to session hi-jacking.
Step 10. Learn More About Website Security
If you want to run a website then it's a good idea to invest some time in learning about website security. We recommend the following online resources and books:
Step 11. Backup Your Website
If you're not already using myRepono to backup your website please sign-up now to ensure your website is regularly backed up. Having a good backup is the ultimate protection against any attack - with myRepono you can restore a damaged website in seconds!
Comments
Post Comment
|  |
 |
 |
Tell us your backup stories!
Have you experienced a backup disaster? Please tell us about all your computing mis-haps and we'll include the best stories in our blog!
|
|